18.1. SSL / TLS for incoming connections
When the browser uses a URL starting with https, rather than http, the connection is encrypted. These days, this is done using a protocol called TLS (transport layer security) although the term SSL (which was the predecessor protocol) is still widely used to refer to secure connections.
18.1.1. Checking for HTTPS support
The first step is to check your web site has HTTPS enabled. To do this, simply go to the front page of your site and then edit the address in the browser so it uses HTTPS instead of HTTP. For example,
https://www.demo.xyz/
If you see an error in your browser that the site is untrusted, or that the connection was interrupted, or any other browser error, then SSL is NOT running properly on your site. You should contact the host or your developer if you believe it should be.
Only once you have verified that HTTPS support is setup and working should you attempt to activate the SSL/TLS support within Kartris.
18.1.2. Activating Kartris's SSL / TLS support
Once logged in to the back end, find the general.security.ssl config setting. There are four possible settings ('always on' SSL was introduced in Kartris v2.7000, 'external' was introduced in Kartris v2.9008).
- 'n' = off
- 'y' = on for pages where sensitive data is transferred (login, checkout, back end, any page when user is logged in)
- 'a' = always on, SSL for all pages
- 'e' = external SSL, applied by a platform like Cloudflare, see @18.1.3. External SSL
Scope of HTTPS
Using HTTPS puts an additional overhead on a web server and a user's browser, and so originally was used only in places where sensitive data is transferred, especially for credit card transactions. There was seen as little point applying it to all traffic such as when a casual visitor is browsing the site, or a search engine is spidering it.
However, in recent years, HTTPS has become more widespread. Many web sites such as Google use it by default, and the revelations by Edward Snowden of pervasive internet surveillance by security agencies have further highlighted the issues of eavesdropping and user-privacy. In summer 2014, Google indicated that it would start to give slight preference in its results to sites running HTTPS, which has led to a surge in the take up of 'always on' HTTPS.
With the arrival of services such as Let's Encrypt and Cloudflare, both of which can provide a free route to HTTPS, there is no reason these days not to implement it.
18.1.3. External SSL
This is the simplest way to add SSL to your web site. You register and set up your domain with Cloudflare.com (or a similar service), then set the nameservers for your domain to point to the ones Cloudflare tells you.
We'd recommend going into the Cloudflare settings and hitting 'pause' so Cloudflare will only serve DNS for the site at first. This will ensure the site continues to work as before (without SSL) until you decide to do the switch. Leave it a day or two, and check that Cloudflare has issued the required secure certificate for your site.
Once it has, you can activate Cloudflare to handle requests for your web site. We suggest for most sites using the 'flexible' SSL setting in Cloudflare, so you can run your web server with just http, which doen't require a secure certificate, and let Cloudflare add the SSL to the front end for you.
Then in the back end of Kartris, you should set the 'general.security.ssl' config setting to 'e' (for external).
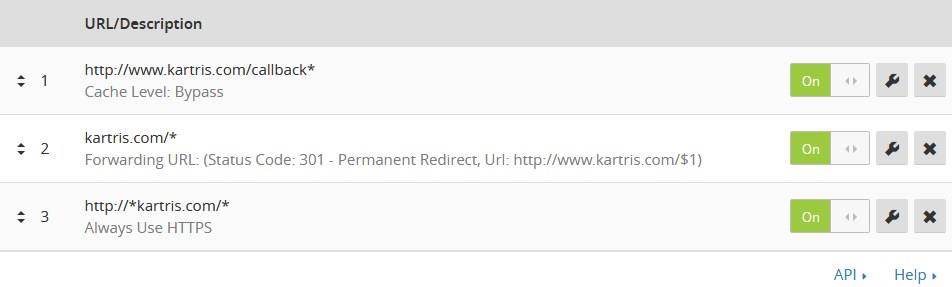
Because Kartris will no longer be able to check programmatically if a page is being called with http or https (it will actually think everything is running http, because there is no SSL at the web server itself), you need to add some page rules into Cloudflare to ensure that appropriate redirection occurs. The ones shown below will redirect http requests to https, and also requests to kartris.com to www.kartris.com. The first request bypasses Cloudflare's cache for payment gateway callbacks to Kartris. This is a good precaution to avoid any unexpected behaviour on those such as redirections, which can prevent them working properly.